CVE-2020-0796¶
描述¶
该漏洞无需授权验证即可被远程利用,可能形成蠕虫级漏洞。目前利用方式是提权
影响版本¶
Windows 10 Version 1903 for 32-bit Systems
Windows 10 Version 1903 for x64-based Systems
Windows 10 Version 1903 for ARM64-based Systems
Windows Server, version 1903 (Server Core installation)
Windows 10 Version 1909 for 32-bit Systems
Windows 10 Version 1909 for x64-based Systems
Windows 10 Version 1909 for ARM64-based Systems
Windows Server, version 1909 (Server Core installation)
只影响 SMB v3.1.1,1903和1909
修复补丁¶
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0796
利用方式¶
这个有点鸡肋特定的windows10 才行还有一个Windows Server 2016
编译方式
- VS2019(V142)X64 Debug
编译好的文件位置
https://github.com/Ascotbe/WindowsKernelExploits/blob/master/CVE-2020-0796/cve-2020-0796-local.exe
环境下载,这边用的是windows 10 Version 1903
ed2k://|file|cn_windows_10_business_editions_version_1903_x64_dvd_e001dd2c.iso|4815527936|47D4C57E638DF8BF74C59261E2CE702D|/
查看MD5值
Get-FileHash -Path c:/windows/system32/drivers/srv2.sys
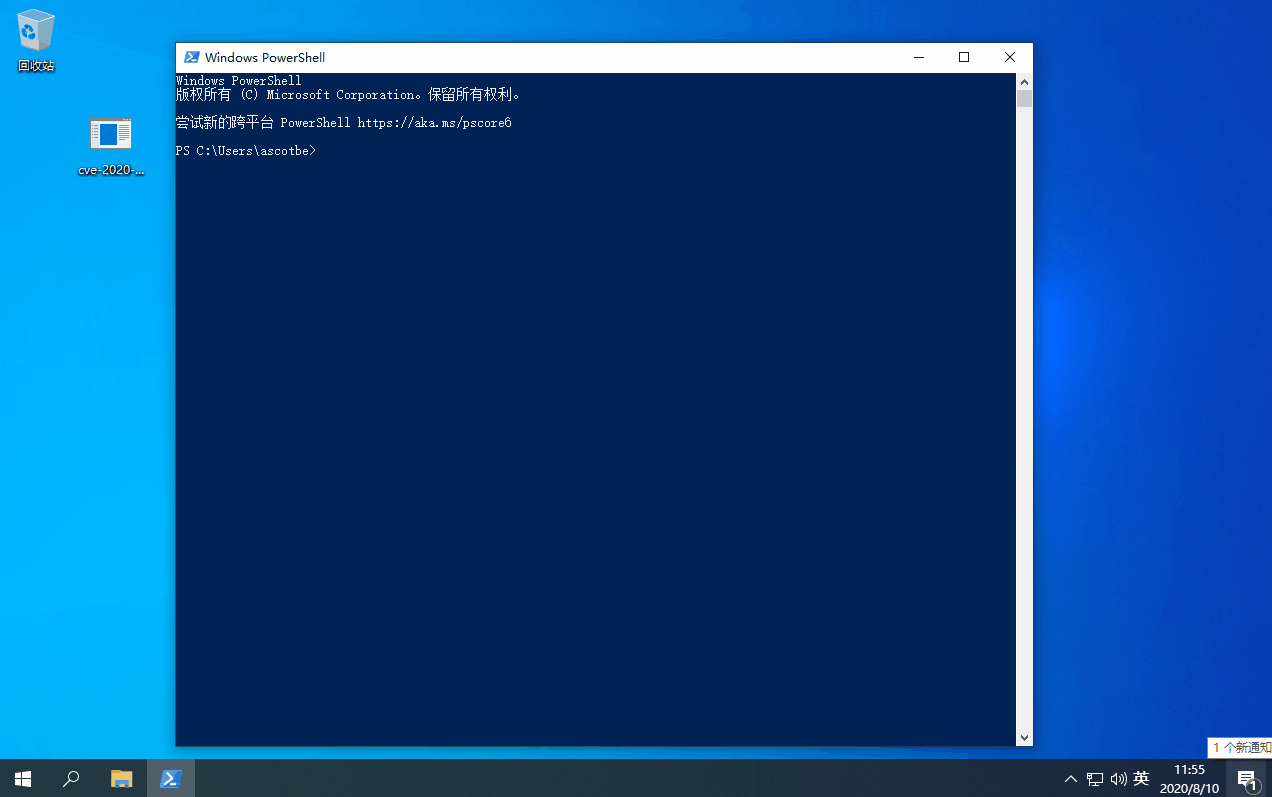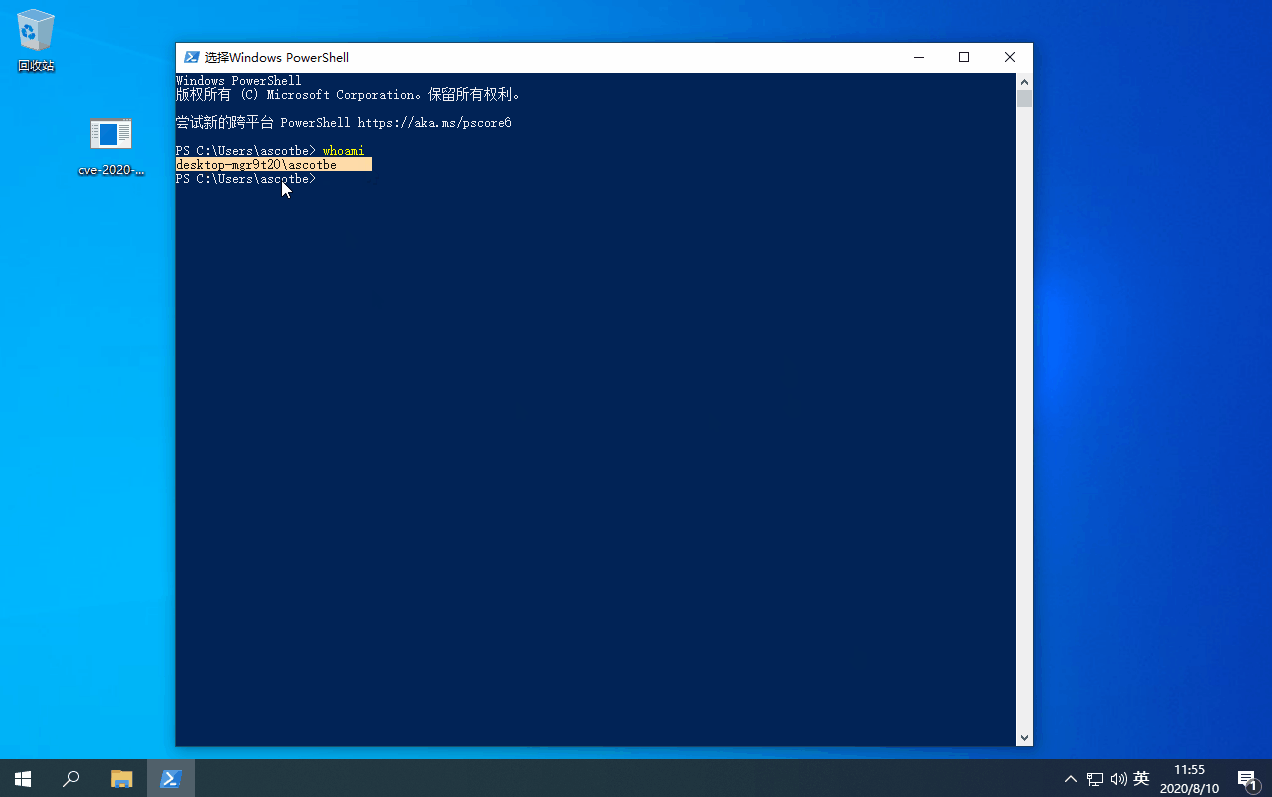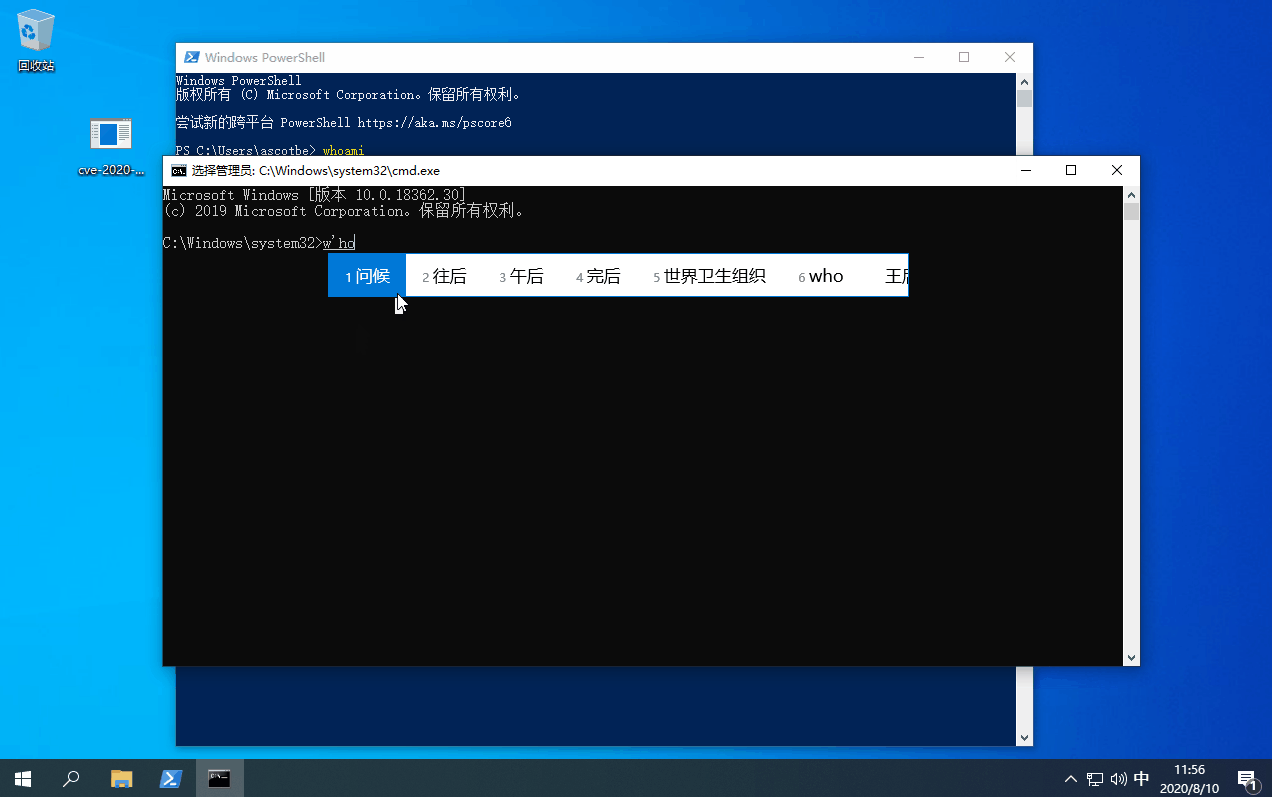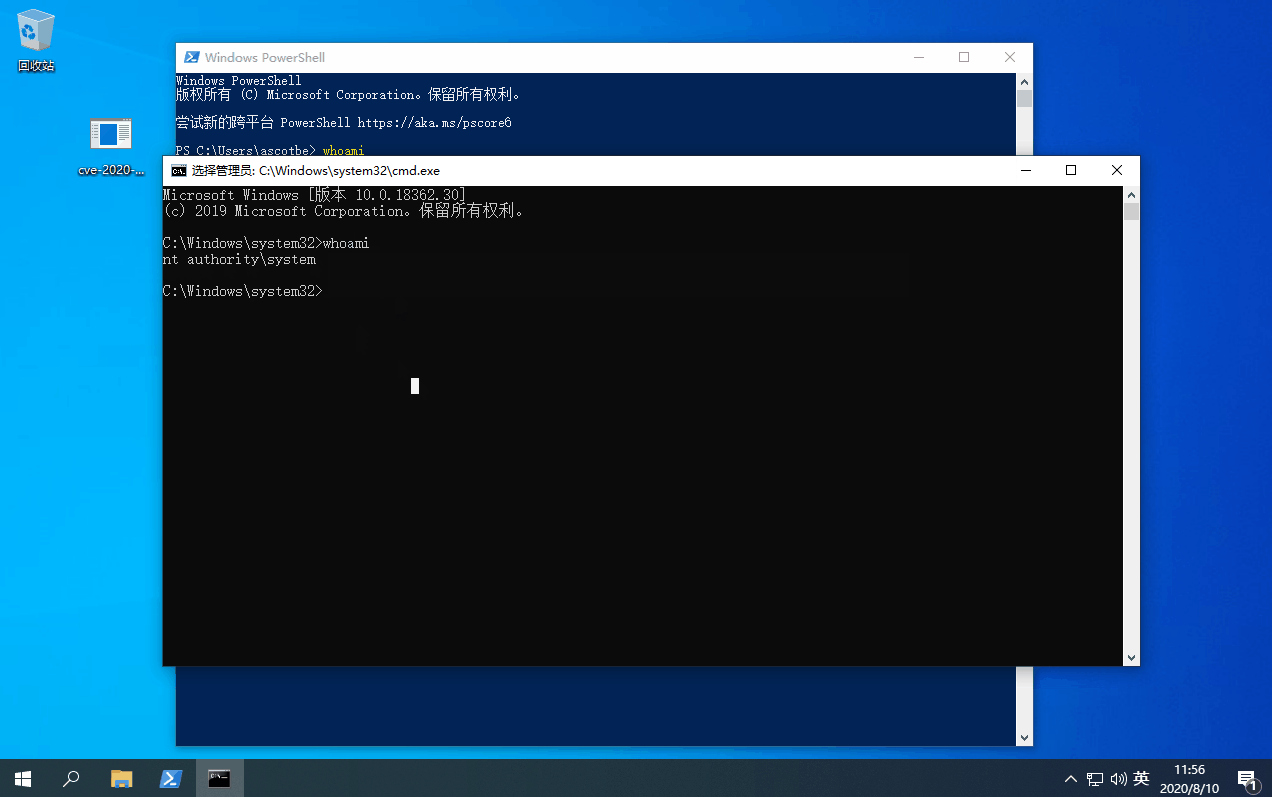
然后就直接上GIF图了
项目来源¶
https://github.com/Ascotbe/Kernelhub/tree/master/CVE-2020-0796